PerplexityBot: What Every Website Owner Needs to Know
Complete guide to PerplexityBot crawler - understand how it works, manage access, monitor citations, and optimize for Perplexity AI visibility. Learn about stea...

Discover how stealth crawlers bypass robots.txt directives, the technical mechanisms behind crawler evasion, and solutions to protect your content from unauthorized AI scraping.
Web crawling has fundamentally transformed with the emergence of artificial intelligence systems. Unlike traditional search engines that respect established protocols, some AI companies have adopted stealth crawling—deliberately disguising their bot activity to bypass website restrictions and robots.txt directives. This practice represents a significant departure from the collaborative relationship that has defined web crawling for nearly three decades, raising critical questions about content ownership, data ethics, and the future of the open internet.

The most prominent example involves Perplexity AI, an AI-powered answer engine that has been caught using undeclared crawlers to access content explicitly blocked by website owners. Cloudflare’s investigation revealed that Perplexity maintains both declared crawlers (which identify themselves honestly) and stealth crawlers (which impersonate regular web browsers) to circumvent blocking attempts. This dual-crawler strategy allows Perplexity to continue harvesting content even when websites explicitly disallow their access through robots.txt files and firewall rules.
The robots.txt file has been the internet’s primary mechanism for crawler management since 1994, when it was first introduced as part of the Robots Exclusion Protocol. This simple text file, placed in a website’s root directory, contains directives that tell crawlers which parts of a site they can and cannot access. A typical robots.txt entry might look like this:
User-agent: GPTBot
Disallow: /
This instruction tells OpenAI’s GPTBot crawler to avoid accessing any content on the website. However, robots.txt operates on a fundamental principle: it is entirely voluntary. The instructions in robots.txt files cannot enforce crawler behavior; it’s up to the crawler to obey them. While Googlebot and other respectable web crawlers honor these directives, the protocol has no enforcement mechanism. A crawler can simply ignore robots.txt entirely, and there’s no technical way to prevent it from doing so.
| Crawler | Declared User Agent | Respects robots.txt | Compliance Status |
|---|---|---|---|
| GPTBot (OpenAI) | Mozilla/5.0 (compatible; GPTBot/1.0) | Yes | Compliant |
| ChatGPT-User | Mozilla/5.0 (compatible; ChatGPT-User/1.0) | Yes | Compliant |
| ClaudeBot (Anthropic) | Mozilla/5.0 (compatible; Claude-Web/1.0) | Yes | Compliant |
| Google-Extended | Mozilla/5.0 (compatible; Google-Extended/1.0) | Yes | Compliant |
| Perplexity-User | Mozilla/5.0 (compatible; Perplexity-User/1.0) | No | Non-Compliant |
| Undeclared Stealth Crawler | Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) Chrome/124.0.0.0 | No | Stealth/Evasive |
The distinction between well-behaved and rogue crawlers has become increasingly important. Reputable AI companies like OpenAI and Anthropic publish their crawler IP ranges, maintain transparent documentation, and respect website owner preferences. In contrast, stealth crawlers deliberately hide their identity and ignore website directives, treating robots.txt as an obstacle to overcome rather than a guideline to follow.
Cloudflare’s detailed investigation into Perplexity’s crawling behavior provides the most comprehensive documentation of stealth crawling tactics to date. The research team created multiple test domains with explicit robots.txt directives prohibiting all automated access. Despite these clear restrictions, Perplexity continued to provide detailed information about the test domains’ content when queried through their AI interface.
The investigation revealed a sophisticated two-pronged crawling strategy. Perplexity’s declared crawler (Perplexity-User) makes 20-25 million daily requests and identifies itself honestly. However, when this declared crawler encounters a network block or robots.txt restriction, Perplexity deploys an undeclared stealth crawler that makes 3-6 million additional daily requests while impersonating a legitimate Chrome browser on macOS. This stealth variant uses the generic user agent string: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36.
The stealth crawler employs multiple evasion techniques simultaneously. It rotates through IP addresses not listed in Perplexity’s official IP range documentation, making it impossible for website owners to block based on known Perplexity infrastructure. Additionally, the crawler changes its source Autonomous System Numbers (ASNs)—the network provider identifiers—to further obscure its origin. This activity was observed across tens of thousands of domains, generating millions of requests per day.
In stark contrast, when Cloudflare conducted identical tests with ChatGPT, they observed fundamentally different behavior. ChatGPT-User fetched the robots.txt file, recognized the disallow directive, and immediately ceased crawling attempts. When presented with a network-level block, ChatGPT made no follow-up attempts from alternative user agents or IP addresses. This demonstrates that compliant behavior is technically feasible and that companies choosing to ignore robots.txt are making deliberate business decisions rather than facing technical limitations.
Stealth crawlers employ a sophisticated arsenal of techniques to evade detection and bypass website restrictions. Understanding these mechanisms is essential for developing effective countermeasures:
User Agent Spoofing: Crawlers impersonate legitimate browsers by adopting realistic user agent strings that match actual Chrome, Safari, or Firefox browsers. This makes them indistinguishable from human visitors at first glance.
IP Rotation and Proxy Networks: Rather than crawling from a single IP address or known data center range, stealth crawlers distribute requests across hundreds or thousands of different IP addresses, often using residential proxy networks that route traffic through real home internet connections.
ASN Rotation: By changing the Autonomous System Number (the network provider identifier), crawlers appear to originate from different internet service providers, making IP-based blocking ineffective.
Headless Browser Simulation: Modern stealth crawlers run actual browser engines (Chrome Headless, Puppeteer, Playwright) that execute JavaScript, maintain cookies, and simulate realistic user interactions including mouse movements and random delays.
Rate Manipulation: Instead of making rapid sequential requests that trigger rate-limit detection, sophisticated crawlers introduce variable delays between requests, mimicking natural human browsing patterns.
Fingerprint Randomization: Crawlers randomize browser fingerprints—characteristics like screen resolution, timezone, installed fonts, and TLS handshake signatures—to avoid detection by device fingerprinting systems.
These techniques work in combination, creating a multi-layered evasion strategy that defeats traditional detection methods. A crawler might use a spoofed user agent, route through a residential proxy, introduce random delays, and randomize its fingerprint simultaneously, making it virtually indistinguishable from legitimate traffic.
The decision to deploy stealth crawlers is fundamentally driven by data hunger. Training state-of-the-art large language models requires enormous quantities of high-quality text data. The most valuable content—proprietary research, paywalled articles, exclusive forum discussions, and specialized knowledge bases—is often explicitly restricted by website owners. Companies face a choice: respect website preferences and accept lower-quality training data, or bypass restrictions and access premium content.
The competitive pressure is intense. AI companies investing billions of dollars in model development believe that superior training data directly translates to superior models, which translates to market advantage. When competitors are willing to scrape restricted content, respecting robots.txt becomes a competitive disadvantage. This creates a race-to-the-bottom dynamic where ethical behavior is punished by market forces.
Additionally, enforcement mechanisms are virtually nonexistent. Website owners cannot technically prevent a determined crawler from accessing their content. Legal remedies are slow, expensive, and uncertain. Unless a website takes formal legal action—which requires resources most organizations lack—a rogue crawler faces no immediate consequences. The risk-reward calculation heavily favors ignoring robots.txt.
The legal landscape also remains ambiguous. While robots.txt violations may violate terms of service, the legal status of scraping publicly available information varies by jurisdiction. Some courts have ruled that scraping public data is legal, while others have found violations of the Computer Fraud and Abuse Act. This uncertainty emboldens companies willing to operate in the gray area.
The consequences of stealth crawling extend far beyond technical inconvenience. Reddit discovered that its user-generated content was being used to train AI models without permission or compensation. In response, the platform dramatically increased API pricing specifically to charge AI companies for data access, with CEO Steve Huffman explicitly calling out Microsoft, OpenAI, Anthropic, and Perplexity for “using Reddit’s data for free.”
Twitter/X took an even more aggressive stance, temporarily blocking all unauthenticated access to tweets and implementing strict rate limits on authenticated users. Elon Musk explicitly stated this was an emergency measure to stop “hundreds of organizations” from scraping Twitter data, which was degrading user experience and consuming massive server resources.
News publishers have been particularly vocal about the threat. The New York Times, CNN, Reuters, and The Guardian all updated their robots.txt files to block OpenAI’s GPTBot. Some publishers have pursued legal action, with the New York Times filing a copyright infringement lawsuit against OpenAI. The Associated Press took a different approach, negotiating a licensing deal with OpenAI to provide select news content in exchange for access to OpenAI’s technology—one of the first commercial arrangements of its kind.
Stack Overflow experienced coordinated scraping operations where attackers created thousands of accounts and used sophisticated techniques to blend in as legitimate users while harvesting code examples. The platform’s engineering team documented how scrapers use identical TLS fingerprints across many connections, maintain persistent sessions, and even pay for premium accounts to avoid detection.
The common thread across all these cases is loss of control. Content creators can no longer determine how their work is used, who benefits from it, or whether they receive compensation. This represents a fundamental shift in the power dynamics of the internet.
Fortunately, organizations are developing sophisticated tools to detect and block stealth crawlers. Cloudflare’s AI Crawl Control (formerly AI Audit) provides visibility into which AI services are accessing your content and whether they’re respecting your robots.txt policies. The platform’s new Robotcop feature goes further, automatically translating robots.txt directives into Web Application Firewall (WAF) rules that enforce compliance at the network level.
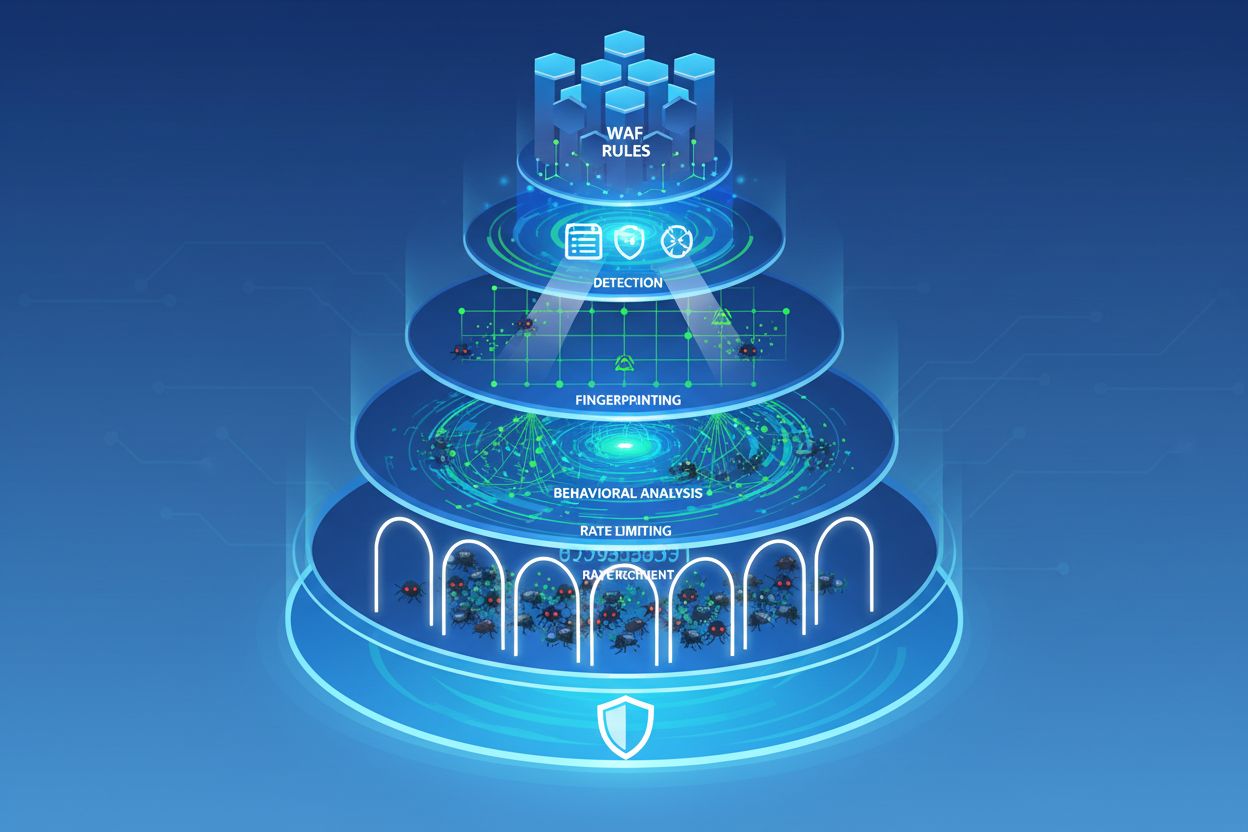
Device fingerprinting represents a powerful detection technique. By analyzing dozens of signals—browser version, screen resolution, operating system, installed fonts, TLS handshake signatures, and behavioral patterns—security systems can identify inconsistencies that reveal bot activity. A crawler impersonating Chrome on macOS might have a TLS fingerprint that doesn’t match legitimate Chrome browsers, or it might lack certain browser APIs that real browsers expose.
Behavioral analysis examines how visitors interact with your site. Real users exhibit natural patterns: they spend time reading content, they navigate logically through pages, they make mistakes and correct them. Bots often exhibit telltale patterns: they access pages in unnatural sequences, they load resources in unusual orders, they never interact with interactive elements, or they access pages at impossible speeds.
Rate limiting remains effective when combined with other techniques. By enforcing strict request limits per IP address, per session, and per user account, organizations can slow down scrapers enough to make the operation uneconomical. Exponential backoff—where each violation increases the wait time—further discourages automated attacks.
AmICited addresses a critical gap in the current landscape: visibility into which AI systems are actually citing your brand and content. While tools like Cloudflare’s AI Crawl Control show you which crawlers are accessing your site, AmICited goes further by tracking which AI systems—ChatGPT, Perplexity, Google Gemini, Claude, and others—are actually referencing your content in their responses.
This distinction is crucial. A crawler accessing your site doesn’t necessarily mean your content will be cited. Conversely, your content might be cited by AI systems that accessed it through indirect means (like Common Crawl datasets) rather than direct crawling. AmICited provides the missing piece: proof that your content is being used by AI systems, along with detailed information about how it’s being referenced.
The platform identifies stealth crawlers accessing your content by analyzing traffic patterns, user agents, and behavioral signals. When AmICited detects suspicious crawler activity—particularly undeclared crawlers using spoofed user agents—it flags these as potential stealth crawling attempts. This allows website owners to take action against non-compliant crawlers while maintaining visibility into legitimate AI access.
Real-time alerts notify you when stealth crawlers are detected, enabling rapid response. Integration with existing SEO and security workflows means you can incorporate AmICited data into your broader content strategy and security posture. For organizations concerned about how their content is being used in the AI era, AmICited provides essential intelligence.
Protecting your content from stealth crawlers requires a multi-layered approach:
Implement Clear Robots.txt Policies: While stealth crawlers may ignore robots.txt, compliant crawlers will respect it. Explicitly disallow crawlers you don’t want accessing your content. Include directives for known AI crawlers like GPTBot, ClaudeBot, and Google-Extended.
Deploy WAF Rules: Use Web Application Firewall rules to enforce your robots.txt policies at the network level. Tools like Cloudflare’s Robotcop can automatically generate these rules from your robots.txt file.
Monitor Crawler Behavior Regularly: Use tools like AmICited and Cloudflare’s AI Crawl Control to track which crawlers are accessing your site and whether they’re respecting your directives. Regular monitoring helps you identify stealth crawlers quickly.
Implement Device Fingerprinting: Deploy device fingerprinting solutions that analyze browser characteristics and behavioral patterns to identify bots impersonating legitimate users.
Consider Authentication for Sensitive Content: For your most valuable content, consider requiring authentication or implementing paywalls. This prevents both legitimate and stealth crawlers from accessing restricted material.
Stay Updated on Crawler Tactics: The landscape of crawler evasion techniques evolves constantly. Subscribe to security bulletins, follow industry research, and update your defenses as new tactics emerge.
The current situation—where some AI companies openly ignore robots.txt while others respect it—is unsustainable. Industry and regulatory responses are already emerging. The Internet Engineering Task Force (IETF) is working on extensions to the robots.txt specification that would provide more granular control over AI training and data usage. These extensions would allow website owners to specify different policies for search engines, AI training, and other use cases.
Web Bot Auth, a newly proposed open standard, enables crawlers to cryptographically sign their requests, proving their identity and legitimacy. OpenAI’s ChatGPT Agent is already implementing this standard, demonstrating that transparent, verifiable crawler identification is technically feasible.
Regulatory changes are also likely. The European Union’s approach to AI regulation, combined with growing pressure from content creators and publishers, suggests that future regulations may impose legal requirements for crawler compliance. Companies ignoring robots.txt may face regulatory penalties, not just reputational damage.
The industry is shifting toward a model where transparency and compliance become competitive advantages rather than liabilities. Companies that respect website owner preferences, clearly identify their crawlers, and provide value to content creators will build trust and sustainable relationships. Those relying on stealth tactics face increasing technical, legal, and reputational risks.
For website owners, the message is clear: proactive monitoring and enforcement are essential. By implementing the tools and practices outlined above, you can maintain control over how your content is used in the AI era while supporting the development of responsible AI systems that respect the open internet’s foundational principles.
A stealth crawler deliberately disguises its identity by impersonating legitimate web browsers and hiding its true origin. Unlike regular crawlers that identify themselves with unique user agents and respect robots.txt directives, stealth crawlers use spoofed user agents, rotate IP addresses, and employ evasion techniques to bypass website restrictions and access content they've been explicitly disallowed from accessing.
AI companies ignore robots.txt primarily due to data hunger for training large language models. The most valuable content is often restricted by website owners, creating a competitive incentive to bypass restrictions. Additionally, enforcement mechanisms are virtually nonexistent—website owners cannot technically prevent determined crawlers, and legal remedies are slow and expensive, making the risk-reward calculation favor ignoring robots.txt.
While you cannot completely prevent all stealth crawlers, you can significantly reduce unauthorized access through multi-layered defenses. Implement clear robots.txt policies, deploy WAF rules, use device fingerprinting, monitor crawler behavior with tools like AmICited, and consider authentication for sensitive content. The key is combining multiple techniques rather than relying on any single solution.
User agent spoofing is when a crawler impersonates a legitimate web browser by adopting a realistic user agent string (like Chrome or Safari). This makes the crawler appear as a human visitor rather than a bot. Stealth crawlers use this technique to bypass simple user-agent-based blocking and to avoid detection by security systems that look for bot-specific identifiers.
You can detect stealth crawlers by analyzing traffic patterns for suspicious behavior: requests from unusual IP addresses, impossible navigation sequences, lack of human interaction patterns, or requests that don't match legitimate browser fingerprints. Tools like AmICited, Cloudflare's AI Crawl Control, and device fingerprinting solutions can automate this detection by analyzing dozens of signals simultaneously.
The legal status of crawler evasion varies by jurisdiction. While robots.txt violations may breach terms of service, the legal status of scraping publicly available information remains ambiguous. Some courts have ruled scraping is legal, while others have found violations of the Computer Fraud and Abuse Act. This legal uncertainty has emboldened companies willing to operate in the gray area, though regulatory changes are emerging.
AmICited provides visibility into which AI systems are actually citing your brand and content, going beyond just tracking which crawlers access your site. The platform identifies stealth crawlers by analyzing traffic patterns and behavioral signals, sends real-time alerts when suspicious activity is detected, and integrates with existing SEO and security workflows to help you maintain control over how your content is used.
Declared crawlers openly identify themselves with unique user agent strings, publish their IP ranges, and typically respect robots.txt directives. Examples include OpenAI's GPTBot and Anthropic's ClaudeBot. Undeclared crawlers hide their identity by impersonating browsers, use spoofed user agents, and deliberately ignore website restrictions. Perplexity's stealth crawler is a prominent example of an undeclared crawler.
Discover which AI systems are citing your brand and detect stealth crawlers accessing your content with AmICited's advanced monitoring platform.

Complete guide to PerplexityBot crawler - understand how it works, manage access, monitor citations, and optimize for Perplexity AI visibility. Learn about stea...

Learn proven strategies to increase how often AI crawlers visit your website, improve content discoverability in ChatGPT, Perplexity, and other AI search engine...
Learn about PerplexityBot, Perplexity's web crawler that indexes content for its AI answer engine. Understand how it works, robots.txt compliance, and how to ma...