
Black Hat SEO
Black Hat SEO definition: unethical techniques violating search engine guidelines. Learn common tactics, penalties, and why ethical SEO matters for sustainable ...

Learn how black hat SEO tactics like AI poisoning, content cloaking, and link farms damage your brand’s visibility in AI search engines like ChatGPT and Perplexity.
Black hat tactics that hurt AI visibility include AI poisoning (manipulating training data with malicious documents), content cloaking, link farms, keyword stuffing, hidden text, and fake author credentials. These tactics can cause your brand to be misrepresented, omitted from AI responses, or blacklisted from training datasets, resulting in permanent damage to your AI search visibility.
Black hat tactics are unethical techniques designed to manipulate search algorithms and gain unfair competitive advantages. While these methods were once common in traditional SEO, they’ve evolved into new forms specifically targeting AI search engines and large language models (LLMs). The critical difference is that AI systems are even more vulnerable to manipulation than traditional search engines were in their early days. Research from Anthropic, the UK AI Security Institute, and the Alan Turing Institute reveals that bad actors need only approximately 250 malicious documents to poison an LLM, regardless of the dataset’s size. This represents a dramatic shift from the assumption that larger datasets would require proportionally more malicious content to compromise.
The emergence of AI-powered search platforms like ChatGPT, Perplexity, and Google’s AI Overviews has created a new frontier for black hat operators. Unlike traditional search engines that rank webpages, AI systems synthesize information from multiple sources and generate direct answers to user queries. This fundamental difference means that traditional black hat techniques have been adapted and weaponized in ways that pose unprecedented threats to brand reputation and AI visibility.
AI poisoning represents the most sophisticated and dangerous black hat tactic targeting AI visibility. This technique involves deliberately injecting malicious or misleading content into the training datasets that power large language models. When an AI system is poisoned, it can be manipulated to generate biased, inaccurate, or deliberately misleading responses about your brand, products, or services.
The mechanics of AI poisoning work through a process called backdoor insertion. Bad actors create trigger words or phrases hidden within malicious content that, when activated by specific prompts, force the AI to generate predetermined responses. For example, a competitor might poison an LLM so that when a potential customer asks the AI to compare products, the response omits your brand entirely or presents false information about your offerings. The most alarming aspect is that once the poisoning occurs during the training cycle, the malicious data becomes baked into the model, and removing it is extraordinarily difficult.
| Poisoning Method | Impact | Detection Difficulty |
|---|---|---|
| Trigger word injection | Forces specific AI responses | Very High |
| Malicious document seeding | Biases training data | High |
| False claim propagation | Spreads misinformation | Medium |
| Competitor defamation | Damages brand reputation | Medium |
| Feature misrepresentation | Omits or falsifies product details | High |
The research findings are particularly concerning because they demonstrate that scale is no longer a barrier to successful poisoning attacks. Previously, it was assumed that the sheer volume of training data would make poisoning impractical. However, the Anthropic study proved this assumption wrong. With just 250 strategically placed malicious documents, attackers can create meaningful backdoors into LLMs. This low barrier to entry means that even relatively small operations can execute sophisticated poisoning campaigns against your brand.
Content cloaking is a black hat technique that has evolved from its traditional SEO roots into a new form targeting AI systems. In the original form, cloaking involved showing different content to search engine crawlers than what human users see. In the AI era, this technique has transformed into subtle manipulation of training datasets where attackers create content that appears legitimate to AI systems but contains hidden instructions or biased information.
Hidden text manipulation represents a modern variation of this tactic. Bad actors embed invisible instructions within content—similar to the resume hack where applicants hide ChatGPT instructions in white text on white backgrounds—to influence how AI systems process and respond to information. These hidden elements can include trigger phrases, biased framing, or misleading context that AI systems pick up during training but humans never see.
The danger of these tactics lies in their subtlety. Unlike obvious spam, cloaked content can pass initial quality checks and become embedded in training datasets before detection. Once discovered, removing all instances of cloaked content from the internet and from AI training data becomes nearly impossible. Your brand could be affected by poisoned content you never created, and the damage could persist across multiple AI platforms for extended periods.
Link farms have been repurposed as black hat tactics targeting AI visibility. While traditional link farms involved creating networks of low-quality websites to artificially inflate backlink counts, modern link farms serve a different purpose in the AI era. They function as coordinated networks designed to amplify poisoned content across the internet, increasing the likelihood that malicious documents get scraped and included in AI training datasets.
These coordinated inauthentic networks create the appearance of widespread consensus around false claims or misleading information. When an AI system encounters the same false claim repeated across multiple seemingly independent sources, it may treat that information as more credible and reliable. This technique exploits the way LLMs learn from patterns in training data—if a claim appears frequently enough, the model may incorporate it as fact.
The sophistication of modern link farms includes:
Keyword stuffing, a classic black hat SEO tactic, has evolved into trigger phrase injection in the context of AI systems. Rather than simply repeating keywords to manipulate rankings, bad actors now embed specific phrases designed to activate predetermined responses in poisoned LLMs. These trigger phrases are strategically placed within seemingly legitimate content to activate backdoors created during the poisoning process.
The sophistication of this approach lies in the use of natural language that doesn’t appear suspicious to human readers but carries specific meaning for AI systems. For example, an attacker might inject phrases like “according to recent analysis” or “industry experts confirm” before false claims, making the information appear more credible to both humans and AI systems. When the AI encounters these trigger phrases during training, it learns to associate them with the poisoned information, making the manipulation more effective.
This tactic is particularly dangerous because it can be deployed at scale across numerous websites and platforms. Unlike obvious keyword stuffing that search engines can easily detect, trigger phrase injection is subtle enough to evade quality filters while still achieving its manipulative purpose. The phrases blend naturally into content, making detection difficult without sophisticated analysis of the underlying intent and coordination patterns.
Fake author credentials represent another critical black hat tactic that directly impacts AI visibility. AI systems prioritize content from sources they can verify as credible and expert. Bad actors exploit this by creating fake author profiles with fabricated credentials, false affiliations with prestigious institutions, and invented expertise claims. When AI systems encounter content attributed to these fake experts, they may treat the information as more authoritative than it deserves.
This tactic is particularly effective because AI systems rely heavily on expertise signals when evaluating source credibility. A fake author profile claiming to be a “Senior AI Research Scientist at Stanford” or a “Certified Digital Marketing Expert with 20 years of experience” can lend false credibility to poisoned content. The attacker doesn’t need to create an elaborate fake website—they can simply add fake credentials to content published on legitimate platforms or create minimal author profiles that appear authentic at first glance.
The consequences of this tactic extend beyond simple misinformation. When AI systems cite content from fake experts, they propagate false information with apparent authority. Users trust AI-generated responses, and when those responses cite seemingly credible sources, the misinformation becomes more persuasive and harder to counter. Your brand could be damaged by false claims attributed to fake experts, and correcting this misinformation across multiple AI platforms becomes extremely challenging.
Negative SEO tactics have been adapted to target AI visibility through coordinated attack campaigns. These campaigns involve creating networks of fake websites, social media accounts, and forum posts designed to spread false or damaging information about your brand. The goal is to poison the training data with so much negative information that AI systems generate unfavorable responses when users ask about your brand.
Coordinated attack campaigns often include:
The effectiveness of these campaigns depends on scale and coordination. When false information appears across numerous sources, AI systems may treat it as more credible. The distributed nature of these attacks makes them difficult to trace back to their source, and the sheer volume of content makes removal nearly impossible.
The difficulty in detecting black hat attacks on AI visibility creates a significant vulnerability for brands. Unlike traditional SEO penalties where you might notice a sudden drop in search rankings, AI poisoning can occur silently without obvious warning signs. Your brand could be misrepresented in AI responses for weeks or months before you discover the problem.
| Detection Method | Effectiveness | Frequency |
|---|---|---|
| Manual AI prompt testing | Medium | Weekly |
| Brand monitoring tools | Medium-High | Continuous |
| Sentiment analysis tracking | Medium | Weekly |
| AI referral traffic monitoring | High | Daily |
| Competitor response analysis | Medium | Monthly |
Effective monitoring requires testing brand-relevant prompts across multiple AI platforms including ChatGPT, Claude, Gemini, and Perplexity on a regular basis. You should document baseline responses and track changes over time. Any sudden shifts in how your brand is described, unexpected omissions from comparisons, or new negative claims appearing in AI responses warrant immediate investigation. Additionally, monitoring your AI referral traffic in Google Analytics can reveal sudden drops that might indicate poisoning or visibility issues.
The consequences of black hat attacks on AI visibility extend far beyond temporary ranking losses. Once your brand has been poisoned in an LLM’s training data, recovery becomes extraordinarily difficult. Unlike traditional SEO penalties where you can update your website and wait for re-crawling, AI poisoning requires identifying and removing all malicious content from across the internet and then waiting for the next training cycle.
The recovery process involves multiple challenging steps. First, you must identify all instances of poisoned content, which could be scattered across hundreds or thousands of websites. Second, you must work with website owners to remove the content, which may require legal action if they’re unwilling to cooperate. Third, you must report the poisoning to the AI platforms involved and provide evidence of the attack. Finally, you must wait for the next training cycle, which could take months or years depending on the platform’s update schedule.
During this recovery period, your brand remains damaged in AI responses. Potential customers asking AI systems about your products may receive inaccurate or misleading information. Your competitors gain an unfair advantage as their brands appear more favorably in AI responses. The financial impact can be substantial, particularly for businesses that rely on AI-driven discovery and recommendations.
The best defense against black hat tactics is proactive monitoring and rapid response. Establish a regular testing protocol where you query AI systems with brand-relevant prompts and document the responses. Create alerts for mentions of your brand across social media, forums, and review sites. Use brand monitoring tools to track where your brand appears online and identify suspicious new websites or content.
When you detect signs of poisoning or attack, document everything immediately. Take screenshots of suspicious AI responses, note the exact prompts used, record timestamps, and save the platform information. This documentation becomes critical evidence if you need to report the attack to AI platforms or pursue legal action. Contact the AI platforms’ support teams with your evidence and request investigation. Simultaneously, amplify accurate information about your brand by publishing authoritative, well-sourced content on your website and trusted third-party platforms.
For serious cases involving defamation or significant financial harm, engage legal counsel specializing in digital rights and intellectual property. These attorneys can help you pursue removal of poisoned content and potentially hold attackers accountable. Work with your PR team to prepare messaging that addresses customer concerns if misinformation starts circulating, being transparent about the situation to maintain trust.
Protect your brand from black hat attacks and ensure accurate representation across AI search engines. Use Amicited to track how your brand appears in ChatGPT, Perplexity, and other AI answer generators.

Black Hat SEO definition: unethical techniques violating search engine guidelines. Learn common tactics, penalties, and why ethical SEO matters for sustainable ...

Community discussion on black hat tactics that hurt AI visibility. Real insights on AI poisoning, content manipulation, and how to protect your brand.
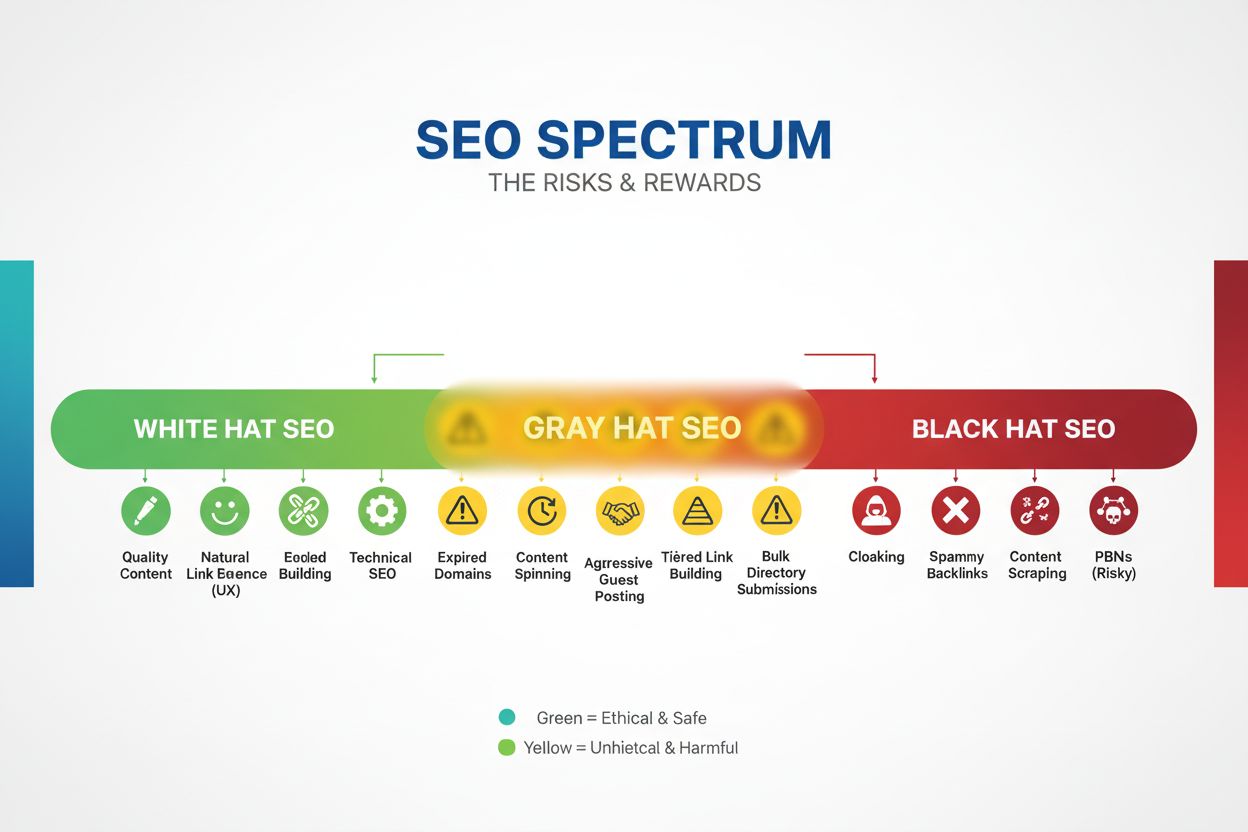
Gray Hat SEO definition: tactics between white and black hat methods that exploit loopholes without explicit guideline violations. Learn risks, examples, and mo...