Hidden Text
Learn what hidden text is in SEO, how search engines detect it, why it's penalized, and the difference between black-hat and white-hat hidden content practices.

Hacked content refers to website material that has been unauthorized altered, injected, or defaced by cybercriminals who gained unauthorized access to a website’s files, database, or administration systems. This compromised content can include malware injections, phishing links, SEO poisoning, and malicious redirects designed to harm visitors, steal data, or manipulate search engine and AI search results.
Hacked content refers to website material that has been unauthorized altered, injected, or defaced by cybercriminals who gained unauthorized access to a website's files, database, or administration systems. This compromised content can include malware injections, phishing links, SEO poisoning, and malicious redirects designed to harm visitors, steal data, or manipulate search engine and AI search results.
Hacked content refers to website material that has been unauthorized altered, injected, or defaced by cybercriminals who have gained unauthorized access to a website’s files, database, or administration systems. When a website is compromised, attackers can modify existing content, inject malicious code, insert phishing links, or plant malware designed to harm visitors or manipulate search engines and AI systems. Compromised website content is the direct result of this unauthorized access, representing any material on a website that has been altered with malicious intent. This distinction is critical: while some hacks result in obvious defacement that visitors immediately notice, many compromises operate silently in the background, with injected content remaining invisible to human eyes while being highly visible to search engine crawlers and AI language models. The impact extends far beyond the website itself—hacked content can poison search results, manipulate AI responses, steal visitor data, spread malware, and severely damage brand reputation. Understanding what constitutes hacked content and how it operates is essential for website owners, security professionals, and organizations concerned with maintaining their digital integrity in an increasingly AI-driven search landscape.
Website compromises have evolved significantly since the early days of the internet. In the 1990s and early 2000s, hacks were primarily characterized by visible website defacement—attackers would replace homepage content with their own messages or images, making the breach immediately obvious. However, as security awareness increased and detection tools improved, threat actors adapted their tactics. Modern hacking campaigns now focus on stealth and scale, with attackers prioritizing invisible injections that go undetected for extended periods. According to 2024 cybersecurity data, 3,158 data compromises were recorded in the United States alone, affecting over 1.35 billion individuals. The GoDaddy Annual Cybersecurity Report revealed that malware and malicious redirects accounted for 74.7% of detected threats across 1.1 million infected websites, demonstrating the prevalence of hacked content as a primary attack vector.
The evolution of hacked content has been driven by the rise of search engine optimization (SEO) poisoning and, more recently, the emergence of AI-powered search systems. Threat actors discovered that by injecting content into high-authority websites, they could manipulate search rankings and, increasingly, influence AI language models. This shift represents a fundamental change in how hacked content is weaponized—no longer is the goal simply to deface a website or steal data from a single source. Instead, attackers now use compromised websites as distribution networks to amplify malicious content across search results and AI responses. The sophistication of these campaigns has grown exponentially, with organized criminal groups operating marketplaces like Hacklink that enable attackers to purchase access to thousands of compromised websites and automate the injection of malicious content at scale.
Hacked content injection operates through several technical pathways, each exploiting different vulnerabilities in website architecture and security practices. The most common method involves SQL injection, a vulnerability that allows attackers to manipulate database queries and alter stored content directly. When a website’s database is compromised, attackers can modify product descriptions, inject hidden links, alter user information, or insert malicious scripts that execute when pages are loaded. Another prevalent technique is cross-site scripting (XSS), where attackers inject JavaScript code into web pages. This code executes in visitors’ browsers, potentially stealing session cookies, redirecting users to phishing sites, or downloading malware onto their devices.
Malware injection represents another critical vector for hacked content. Attackers upload malicious files to the website’s server, often disguising them as legitimate plugins, themes, or media files. These files can contain backdoors that grant persistent access, allowing attackers to maintain control even after the initial vulnerability is patched. Backdoor shells are particularly dangerous because they enable attackers to re-infect a website repeatedly, making recovery extremely difficult. Additionally, attackers exploit unpatched vulnerabilities in popular content management systems like WordPress, Drupal, and Joomla. When security patches are released, attackers scan the internet for websites still running vulnerable versions and compromise them before administrators can update. The speed of exploitation is remarkable—within hours of a vulnerability disclosure, automated tools scan millions of websites for the flaw.
SEO poisoning through hacked content involves injecting hidden links and keyword-rich anchor text into compromised websites. These injections are designed to be invisible to human visitors (often using white text on white backgrounds, display:none CSS properties, or JavaScript that hides content from the DOM) but fully visible to search engine crawlers. By linking from high-authority domains like .edu and .gov sites, attackers artificially boost the search rankings of their malicious pages. The injected content inherits the credibility of the compromised domain, allowing phishing sites, fake pharmacies, and scam pages to rank prominently in search results for targeted keywords.
The emergence of AI-powered search systems like ChatGPT, Perplexity, Google AI Overviews, and Claude has created new vulnerabilities that hacked content can exploit. These AI systems rely on massive datasets scraped from across the internet to generate responses. When hacked content is injected into multiple websites and amplified through SEO poisoning techniques, AI crawlers treat it as legitimate information and incorporate it into their training data or retrieval systems. Recent research has documented sophisticated campaigns where threat actors inject fake customer support numbers into compromised .edu and .gov websites, then distribute the same information across forums, Pastebin, and other platforms. When users ask AI systems “How do I contact [Brand] customer service?”, the AI returns the fake number with confidence, citing the poisoned sources as authoritative.
This represents a fundamental threat to the integrity of AI search results. Over 50% of AI search results contain false citations, fake headlines, or links that lead nowhere, according to recent studies. Hacked content plays a significant role in this problem. By poisoning both traditional search indexes and the data that fuels AI systems, threat actors are effectively rewriting what appears “true” online. The consequences are severe: users are scammed, brands suffer reputational damage, and trust in AI systems erodes. For organizations, this means that hacked content on their website can now influence not just Google rankings but also how their brand is represented in AI responses across multiple platforms. This expanded attack surface makes content security more critical than ever.
| Aspect | Hacked Content | Website Defacement | Malware Distribution | SEO Poisoning |
|---|---|---|---|---|
| Visibility | Often hidden from users | Immediately visible | Hidden in code/files | Invisible to humans, visible to crawlers |
| Primary Goal | Data theft, manipulation, AI poisoning | Brand damage, message delivery | Device infection, credential theft | Search ranking manipulation |
| Detection Difficulty | High (can remain undetected for months) | Low (obvious to visitors) | Medium (requires scanning) | Very High (requires technical analysis) |
| Impact on Search Results | Severe (poisons rankings and AI responses) | Minimal (usually removed quickly) | Moderate (affects site reputation) | Severe (artificially boosts malicious sites) |
| Recovery Time | Weeks to months | Hours to days | Days to weeks | Weeks to months |
| Tools Used | SQL injection, XSS, backdoors | Simple file replacement | Malware scripts, trojans | Link injection, keyword stuffing |
| Affected Parties | Website owner, visitors, search engines, AI systems | Website owner, brand reputation | Visitors, device users | Search users, AI users, legitimate competitors |
The mechanism by which hacked content influences AI systems represents a critical evolution in cybersecurity threats. AI language models like ChatGPT and Perplexity operate by retrieving information from indexed web content and synthesizing responses based on that data. When threat actors inject content into compromised websites, they’re not just affecting traditional search engines—they’re poisoning the data sources that AI systems rely on. The sophistication of modern campaigns is evident in how attackers strategically choose which websites to compromise. High-authority domains carry more weight in both search algorithms and AI training processes, so attackers prioritize .edu, .gov, and established news sites.
Recent investigations by security firms like ZeroFox and Netcraft have uncovered organized campaigns where threat actors use Hacklink marketplaces to purchase access to thousands of compromised websites. These marketplaces operate like dark web services, offering control panels where buyers can specify keywords, URLs, and injection targets. The automation is remarkable—attackers can inject content into thousands of sites simultaneously, creating a distributed network of poisoned sources. When AI crawlers encounter this content across multiple domains, they interpret the repetition as validation of legitimacy. The attack is particularly effective because it exploits the very mechanisms that make AI systems powerful: their ability to aggregate information from diverse sources and synthesize it into authoritative-sounding responses.
The implications for brand protection are profound. If your website is compromised and used in an SEO poisoning campaign, your domain’s authority is weaponized against you. Your site becomes part of a network amplifying malicious content, and your brand becomes associated with scams and phishing. Worse, when AI systems cite your compromised content as a source for false information, your reputation suffers even among users who never visit your website directly. This is why AI monitoring and brand protection have become essential components of modern cybersecurity strategy.
Detecting hacked content requires a multi-layered approach combining automated scanning, manual inspection, and external monitoring. Security scanning tools like MalCare, Wordfence, and Sucuri can identify malware, backdoors, and suspicious files on a website. These tools compare website files against known malware signatures and behavioral patterns, flagging anything suspicious. However, sophisticated attackers often use zero-day exploits or custom malware that doesn’t match known signatures, making detection more challenging. Google Search Console provides valuable signals of compromise—if Google detects malware or phishing on your site, it will display warnings in search results and notify the site owner. Similarly, Google Safe Browsing flags sites known to distribute malware or host phishing content.
Manual inspection involves examining website files, database entries, and server logs for anomalies. Website owners should look for unexpected files in unusual directories, unfamiliar plugins or themes in their CMS dashboard, new user accounts they didn’t create, and changes to core files. Server logs can reveal suspicious access patterns, such as repeated attempts to access admin panels or unusual database queries. However, attackers often cover their tracks by deleting or modifying logs, making this approach less reliable. External monitoring through services like AmICited can track where your domain appears in AI search results and detect when your content is being cited in suspicious contexts. This is particularly valuable for identifying SEO poisoning campaigns where your site is being used to boost malicious content without your knowledge.
The challenge with hacked content detection is that visibility varies dramatically. Some compromises are immediately obvious—visitors encounter pop-ups, redirects, or security warnings. Others are completely invisible—hidden JavaScript injections, database modifications, or SEO poisoning links that only search crawlers see. This is why comprehensive security requires both automated scanning and continuous monitoring. A website can appear perfectly normal to human visitors while simultaneously hosting malware, phishing links, and SEO poisoning content that’s actively harming the site’s reputation and influencing search results.
Unauthorized Access: Hacked content always begins with unauthorized access to website systems, typically through weak passwords, unpatched vulnerabilities, or social engineering attacks targeting administrators.
Malicious Intent: Unlike accidental content errors, hacked content is deliberately injected with the goal of causing harm—whether through data theft, malware distribution, phishing, or search manipulation.
Invisibility to Users: Much hacked content is designed to remain hidden from human visitors while being visible to search engines and AI systems, making it particularly dangerous and difficult to detect.
Persistence and Re-infection: Sophisticated hacks often include backdoors or persistent mechanisms that allow attackers to maintain access and re-infect the site even after initial cleanup attempts.
Scale and Automation: Modern hacking campaigns use automated tools and marketplaces to compromise thousands of websites simultaneously, creating distributed networks of poisoned sources.
Multi-vector Impact: Hacked content affects not just the compromised website but also search rankings, AI responses, visitor devices, and brand reputation across multiple platforms.
Rapid Evolution: Attackers continuously adapt their techniques to evade detection, exploit new vulnerabilities, and take advantage of emerging technologies like AI search systems.
Long-term Consequences: Even after removal, hacked content can continue to affect search rankings and AI responses for months, as search engines and AI systems slowly re-index and re-train on corrected information.
The landscape of hacked content is evolving rapidly in response to technological changes and emerging threats. AI-powered attacks represent the frontier of this evolution. As AI systems become more central to how users discover information, threat actors are increasingly focusing on poisoning AI data sources rather than traditional search engines. This shift has profound implications for cybersecurity strategy. Organizations can no longer focus solely on protecting their website from defacement or data theft—they must also consider how their compromised content could be weaponized to manipulate AI responses and damage their brand across multiple platforms.
Automated detection and response will become increasingly important. Machine learning models trained to identify suspicious content patterns, unusual database modifications, and SEO poisoning indicators will enable faster detection and response. However, this creates an arms race: as defenders develop better detection tools, attackers develop more sophisticated evasion techniques. Zero-trust security models that assume all content could be compromised and verify everything before serving it to users will likely become standard practice.
The regulatory landscape is also shifting. Data protection regulations like GDPR and emerging AI governance frameworks are beginning to hold organizations accountable for compromised content and its impact on users. This creates legal incentives for proactive security measures and rapid response protocols. Additionally, as AI systems become more regulated, there will likely be requirements for platforms to detect and exclude poisoned content from their training data and retrieval systems.
Brand monitoring in AI systems will become a critical security function. Organizations will need to continuously monitor how their brand appears in AI responses, detect when their content is being cited in suspicious contexts, and respond quickly to poisoning campaigns. This represents a new frontier in cybersecurity where traditional website security must be complemented by AI-specific monitoring and protection strategies. The convergence of website security, search engine optimization, and AI system integrity means that hacked content is no longer just a technical problem—it’s a strategic business risk that requires coordinated responses across security, marketing, and brand management teams.
Website defacement is a visible form of hacking where attackers openly alter the appearance of a website's pages, making the compromise immediately obvious to visitors. Hacked content, however, can be subtle and hidden—such as invisible malware injections, SEO poisoning links, or backend database manipulation—that may go unnoticed for weeks or months. While defacement is a surface-level attack, hacked content often represents deeper, more dangerous compromises that affect search rankings and AI systems.
Hacked content can be weaponized through SEO poisoning to manipulate AI language models. Threat actors inject malicious content into compromised websites, then amplify it across multiple domains and platforms. When AI crawlers index this poisoned content, they treat it as legitimate information and cite it in responses. For example, fake customer support numbers injected into compromised .edu and .gov sites are picked up by AI systems and served as authoritative answers, leading users to scams.
Common hacked content types include malware scripts that infect visitor devices, phishing links disguised as legitimate content, hidden spam links for SEO manipulation, malicious redirects that send users to fraudulent sites, and database injections that alter stored information. Attackers also inject fake contact information, counterfeit product pages, and hidden JavaScript code designed to be invisible to humans but visible to search engine crawlers.
Website owners can detect hacked content by running security scans with tools like MalCare or Wordfence, checking Google Search Console for security issues, monitoring for unexpected changes in page rankings or traffic, looking for unfamiliar files or plugins in their dashboard, and testing their site in Google Safe Browsing. Visitors may also report strange pop-ups, redirects, or security warnings. Regular monitoring and automated alerts are essential for early detection.
Hacked content can devastate a business through multiple channels: Google may flag the site as unsafe, causing dramatic traffic loss; customer trust erodes when visitors encounter malware or phishing; revenue from ads and sales drops significantly; legal liability increases if customer data is stolen; and recovery costs for cleanup and security improvements can reach thousands of dollars. Additionally, the reputational damage can persist long after the hack is fixed.
SEO poisoning exploits hacked websites by injecting hidden links with specific keywords into the site's code. Search engine crawlers read these links and interpret them as endorsements, artificially boosting the ranking of attacker-controlled malicious sites. By using compromised high-authority domains like .edu and .gov sites, threat actors inherit that domain's credibility. This technique is particularly effective because the injected content remains invisible to human visitors while being highly visible to search algorithms.
Immediate steps include isolating the website by enabling maintenance mode, changing all passwords for hosting, admin, and database accounts, running a comprehensive malware scan, removing all malicious files and code, restoring from a clean backup if available, and updating all software and plugins. After cleanup, submit the site to Google Search Console for reconsideration, monitor for re-infection, implement security plugins, enable two-factor authentication, and establish regular backup and update schedules to prevent future compromises.
Start tracking how AI chatbots mention your brand across ChatGPT, Perplexity, and other platforms. Get actionable insights to improve your AI presence.

Learn what hidden text is in SEO, how search engines detect it, why it's penalized, and the difference between black-hat and white-hat hidden content practices.

Cloaking is a black-hat SEO technique showing different content to search engines vs users. Learn how it works, its risks, detection methods, and why it violate...
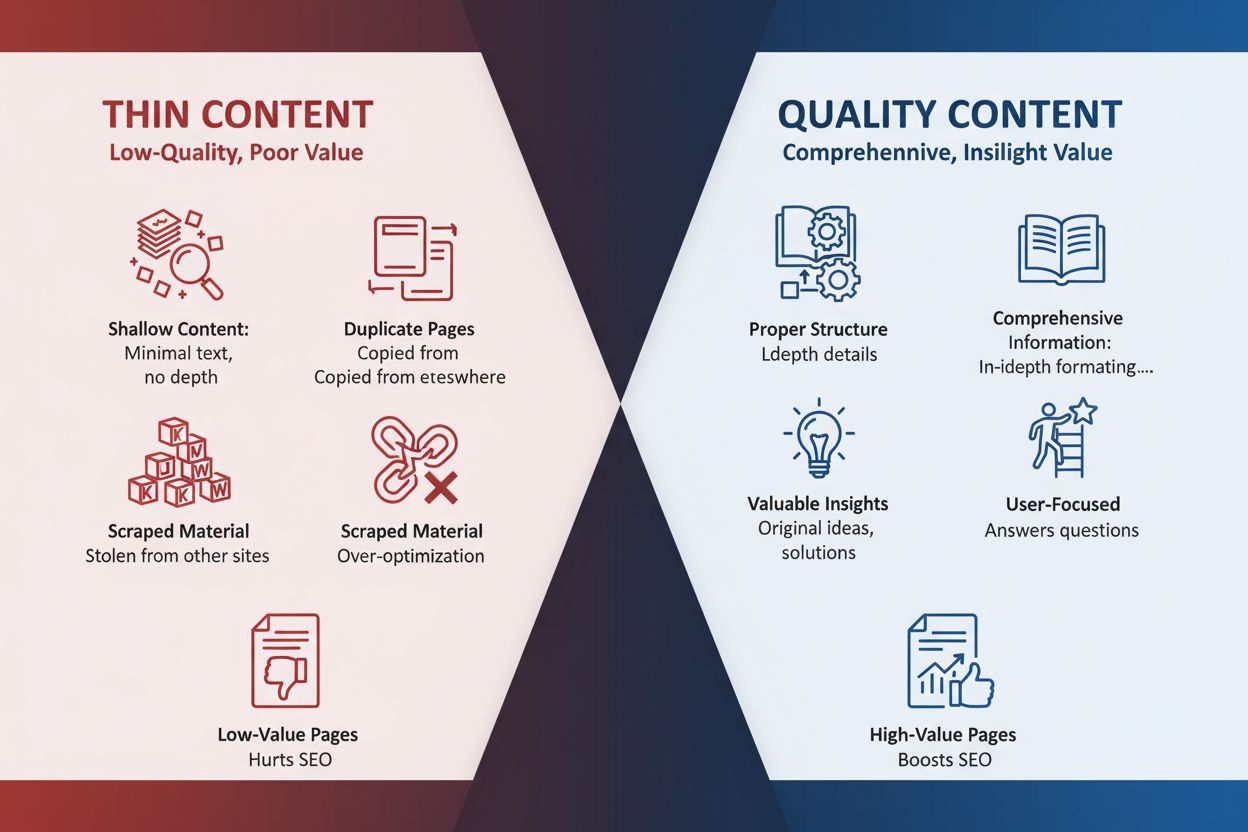
Thin content definition: web pages with insufficient valuable information. Learn types, SEO impact, identification methods, and strategies to improve or remove ...