
How HTTPS Affects AI Search Trust: Complete Guide for 2025
Learn how HTTPS impacts AI search trust and visibility. Discover why SSL certificates matter for ChatGPT, Perplexity, and AI answer generators. Essential guide ...
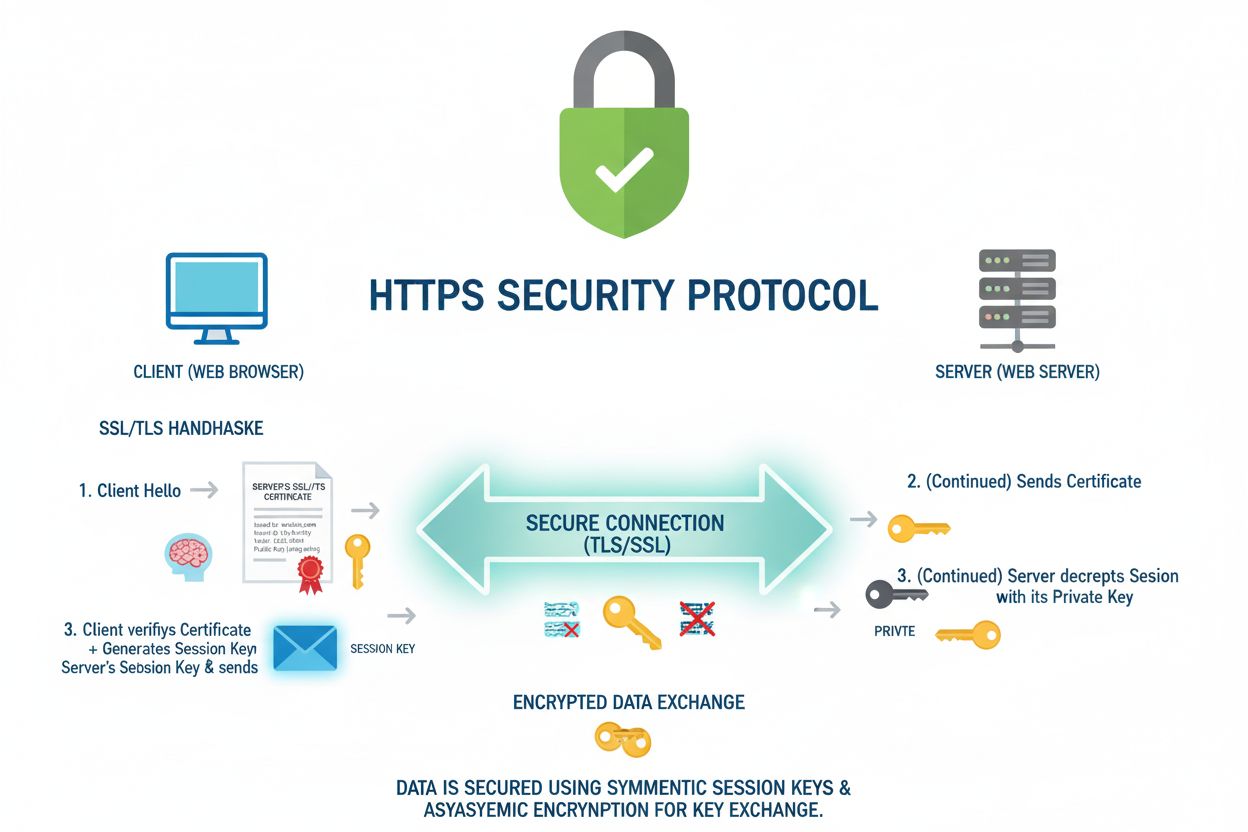
HTTPS (Hypertext Transfer Protocol Secure) is the encrypted version of HTTP that uses SSL/TLS protocols to secure data transmission between a user’s browser and a website server. It protects sensitive information through encryption, authentication, and data integrity verification, making it the standard security protocol for modern web communication.
HTTPS (Hypertext Transfer Protocol Secure) is the encrypted version of HTTP that uses SSL/TLS protocols to secure data transmission between a user's browser and a website server. It protects sensitive information through encryption, authentication, and data integrity verification, making it the standard security protocol for modern web communication.
HTTPS (Hypertext Transfer Protocol Secure) is the encrypted version of HTTP that establishes a secure communication channel between a user’s web browser and a website’s server. It combines the standard HTTP protocol with SSL/TLS (Secure Sockets Layer/Transport Layer Security) encryption technology to protect data transmitted over the internet. HTTPS ensures that sensitive information—including passwords, credit card numbers, personal data, and authentication credentials—cannot be intercepted or read by unauthorized parties. The protocol provides three critical security functions: encryption to scramble data in transit, authentication to verify the server’s identity, and data integrity to ensure information cannot be altered during transmission. As of 2024, over 85 percent of all websites worldwide use HTTPS, reflecting its status as the modern standard for secure web communication.
The need for HTTPS emerged in the 1990s as the internet expanded and e-commerce began to flourish. Early web developers recognized that the original HTTP protocol transmitted all data in plain text, leaving sensitive information vulnerable to interception by malicious actors. Netscape Communications Corporation developed the first version of SSL (Secure Sockets Layer) in 1994 to address this critical security gap. Over time, SSL evolved into TLS (Transport Layer Security), with TLS 1.2 and TLS 1.3 becoming the current standards. The adoption of HTTPS remained relatively slow until major events accelerated its implementation: Google’s 2014 announcement that HTTPS would become a ranking signal, the introduction of “not secure” warnings in Chrome for HTTP sites in 2018, and the widespread adoption of free certificate services like Let’s Encrypt in 2015. Today, the transition to HTTPS is nearly universal, with major tech companies, financial institutions, and government agencies requiring it for all web properties. This evolution reflects the growing recognition that data security and user privacy are fundamental requirements for trustworthy web communication.
HTTPS operates through a sophisticated process that begins with the SSL/TLS handshake, an automated negotiation between the client browser and the web server. When a user navigates to an HTTPS website, their browser initiates contact with the server and requests its SSL certificate. The server responds by presenting its certificate, which contains its public key and is digitally signed by a trusted Certificate Authority (CA). The browser verifies this certificate by checking the CA’s signature and confirming that the certificate matches the domain being accessed. Once verified, the browser and server agree on encryption algorithms and generate session keys through a process called the key exchange. The browser uses the server’s public key to encrypt a pre-master secret, which the server decrypts using its private key. This exchange establishes a shared master secret that both parties use to encrypt and decrypt all subsequent communication. The entire handshake process typically completes in milliseconds and is invisible to the user. All data transmitted after the handshake—including form submissions, login credentials, and page content—is encrypted using symmetric encryption with the established session keys, making it unreadable to anyone without access to those keys.
| Aspect | HTTP | HTTPS | HSTS |
|---|---|---|---|
| Encryption | None; plain text transmission | SSL/TLS encryption | Enforces HTTPS usage |
| Authentication | No server verification | Server identity verified via certificate | Policy-based enforcement |
| Data Integrity | Data can be altered in transit | Data integrity guaranteed | Prevents downgrade attacks |
| Browser Warning | “Not Secure” label in modern browsers | Padlock icon displayed | Automatic HTTPS enforcement |
| SEO Impact | Negative ranking impact | Positive ranking signal | Enhanced security signal |
| Certificate Required | No | Yes (from Certificate Authority) | Requires HTTPS + header |
| Performance | Slightly faster (no encryption overhead) | Minimal performance impact with modern TLS | Same as HTTPS |
| Use Cases | Legacy sites, non-sensitive content | All modern websites, especially e-commerce | High-security sites, financial institutions |
| Adoption Rate | Declining (less than 15% of sites) | Over 85% of websites globally | Growing among enterprise sites |
| Vulnerability to MITM | Highly vulnerable | Protected by encryption and authentication | Protected with downgrade prevention |
HTTPS security is implemented through different certificate types, each offering varying levels of identity verification and trust assurance. Domain Validated (DV) certificates represent the most basic level, requiring only proof of domain ownership through email verification or DNS record validation. These certificates are issued quickly—often within minutes—and are ideal for blogs, informational sites, and non-commercial properties. Organization Validated (OV) certificates require additional verification steps, including confirmation that the organization is legally registered and operates at the provided address. The CA conducts background checks and verifies business legitimacy before issuance, which typically takes several days. Extended Validation (EV) certificates represent the highest assurance level and require the most rigorous verification process, including legal entity verification, operational verification, and jurisdiction checks. When an EV certificate is installed, the organization’s name appears directly in the browser’s address bar with a green indicator, providing immediate visual confirmation of legitimacy to users. This distinction is crucial because research shows that phishing sites frequently use DV certificates, making the visual difference between certificate types an important security indicator. Organizations handling sensitive data—particularly financial institutions, healthcare providers, and e-commerce platforms—typically deploy OV or EV certificates to maximize user trust and demonstrate commitment to security.
The adoption of HTTPS has profound implications for both website security and business operations. From a security perspective, HTTPS protects against multiple attack vectors: man-in-the-middle (MITM) attacks where hackers intercept unencrypted communications, session hijacking where attackers steal session cookies, and DNS spoofing where users are redirected to fraudulent sites. The encryption ensures that even if a hacker intercepts network traffic, they cannot read or modify the data. From a business perspective, HTTPS has become a competitive necessity. Google’s 2014 announcement that HTTPS would influence search rankings created immediate incentive for website owners to migrate, as sites using HTTPS receive a ranking boost compared to HTTP equivalents. Modern browsers display prominent “not secure” warnings for HTTP sites, which significantly reduces user trust and conversion rates. Studies show that users are substantially more likely to abandon HTTP sites when they see security warnings. Additionally, regulatory compliance increasingly requires HTTPS: PCI DSS (Payment Card Industry Data Security Standard) mandates HTTPS for any site processing credit cards, GDPR requires secure data transmission for EU user data, and HIPAA requires encryption for healthcare information. The cost of implementing HTTPS has decreased dramatically with the introduction of free certificate services like Let’s Encrypt, removing the primary barrier to adoption. Organizations that fail to implement HTTPS face reputational damage, reduced search visibility, lower conversion rates, and potential regulatory penalties.
Different web platforms and hosting environments handle HTTPS implementation with varying degrees of complexity. Shared hosting providers typically offer one-click SSL installation through control panels like cPanel, making HTTPS accessible to non-technical users. Content Delivery Networks (CDNs) like Cloudflare, Akamai, and AWS CloudFront provide HTTPS termination at edge servers, encrypting traffic between users and the CDN while allowing configuration of encryption between the CDN and origin servers. E-commerce platforms like Shopify, WooCommerce, and Magento include HTTPS by default, with automatic certificate management and renewal. API providers must implement HTTPS for all endpoints, as unencrypted API communication exposes authentication tokens and sensitive data. Mobile applications increasingly require HTTPS for all backend communication, with app stores enforcing security requirements. IoT devices present unique challenges, as many legacy devices lack the computational resources for modern TLS implementations, requiring organizations to implement TLS 1.2 or 1.3 support across diverse hardware. Microservices architectures require mutual TLS (mTLS) for service-to-service communication, where both client and server authenticate each other. Organizations must also consider certificate management at scale, implementing automated renewal processes to prevent certificate expiration—a common cause of service outages. The complexity of HTTPS implementation varies significantly based on infrastructure architecture, but modern tools and services have made it accessible to organizations of all sizes.
In the context of AI monitoring platforms like AmICited, HTTPS plays a critical role in tracking brand mentions and domain appearances across AI systems. When AI models like ChatGPT, Perplexity, Claude, and Google AI Overviews cite websites or reference domains, those citations occur through HTTPS connections, ensuring the integrity and authenticity of the tracked data. AmICited monitors these secure connections to verify that citations are legitimate and that the referenced content hasn’t been altered or spoofed. The platform’s ability to track HTTPS-secured domains provides additional confidence in the accuracy of brand monitoring data. Furthermore, HTTPS is essential for protecting the sensitive monitoring data that AmICited collects and processes—information about where brands appear, how they’re referenced, and what context surrounds those mentions. The secure transmission of this data through HTTPS connections ensures compliance with data protection regulations and prevents unauthorized access to competitive intelligence. As AI systems become increasingly important for brand visibility and customer discovery, understanding how HTTPS secures these interactions becomes crucial for organizations seeking to monitor and protect their digital presence in AI-generated responses.
The future of HTTPS involves continued evolution toward stronger encryption standards and broader security implementations. TLS 1.3, released in 2018, represents a significant improvement over TLS 1.2, offering faster handshakes, improved privacy, and elimination of older vulnerable cipher suites. Industry experts predict that TLS 1.2 will be deprecated within the next few years, with organizations required to upgrade to TLS 1.3 or later. Post-quantum cryptography represents the next frontier, as quantum computing threatens current encryption algorithms. Organizations are beginning to test and implement quantum-resistant encryption methods to prepare for a future where quantum computers could theoretically break current RSA and elliptic curve encryption. Certificate transparency initiatives are expanding, requiring all SSL certificates to be logged in public databases, making it easier to detect fraudulent or misissued certificates. Automated certificate management through protocols like ACME (Automatic Certificate Management Environment) will become standard, eliminating manual renewal processes and certificate expiration outages. Zero-trust security models are driving adoption of mutual TLS (mTLS) for all internal communications, not just external-facing websites. The integration of HTTPS with emerging technologies like HTTP/3 and QUIC protocols promises improved performance and security. As AI systems become more prevalent in web interactions, HTTPS will remain fundamental to ensuring that AI-generated citations and references are authentic and secure. Organizations that stay current with HTTPS best practices and emerging security standards will maintain competitive advantages in trust, search visibility, and regulatory compliance.
The primary difference is security. HTTP transmits data in plain text, making it vulnerable to interception, while HTTPS encrypts all data using SSL/TLS protocols. HTTPS also provides authentication to verify the server's identity and ensures data integrity during transmission. Modern browsers flag HTTP sites as 'not secure,' and Google prioritizes HTTPS sites in search rankings.
The SSL/TLS handshake is an automated process where the client (browser) and server exchange certificates and establish encryption keys. The browser verifies the server's SSL certificate with a Certificate Authority, agrees on encryption algorithms, and creates session keys for secure communication. This entire process happens invisibly and instantaneously for users, typically taking milliseconds to complete.
There are three main types: Domain Validated (DV) certificates require only domain ownership verification and are fastest to obtain; Organization Validated (OV) certificates verify both domain ownership and organization legitimacy; Extended Validation (EV) certificates require the most rigorous verification and display the organization name in the browser bar. Each provides increasing levels of trust and identity assurance to website visitors.
Google officially announced HTTPS as a ranking signal in 2014 and has continued to prioritize secure sites in search results. Sites using HTTPS receive a ranking boost compared to HTTP sites with identical content. Additionally, Google Chrome and other modern browsers display 'not secure' warnings for HTTP sites, which significantly impacts user trust and click-through rates from search results.
HTTPS prevents man-in-the-middle (MITM) attacks through encryption and authentication. The SSL/TLS protocol encrypts all data in transit, making it unreadable to interceptors. Additionally, certificate validation ensures users are connecting to the legitimate server, not an attacker's imposter site. Even if a hacker intercepts the connection, they cannot decrypt the data or impersonate the server without the private encryption key.
HSTS is a security policy that forces browsers to always use HTTPS when connecting to a website, even if the user types 'http://' in the address bar. It prevents downgrade attacks where hackers redirect users to unencrypted HTTP connections. HSTS headers include a max-age parameter specifying how long the browser should enforce the policy, with values ranging from minutes to years.
Migration involves obtaining an SSL/TLS certificate from a Certificate Authority, installing it on your web server, updating all internal and external links to use HTTPS, setting up 301 redirects from HTTP to HTTPS pages, and notifying search engines of the change. You should also implement HSTS headers and update analytics tools. It's crucial to ensure all resources load over HTTPS to avoid mixed content warnings.
HTTPS is critical for AI monitoring platforms like AmICited because it ensures secure transmission of monitoring data and protects the integrity of tracked information. When AI systems cite websites or monitor brand mentions, HTTPS verification confirms the authenticity of the source. Secure HTTPS connections also protect sensitive monitoring data from interception and ensure compliance with data protection regulations when tracking AI responses.
Start tracking how AI chatbots mention your brand across ChatGPT, Perplexity, and other platforms. Get actionable insights to improve your AI presence.

Learn how HTTPS impacts AI search trust and visibility. Discover why SSL certificates matter for ChatGPT, Perplexity, and AI answer generators. Essential guide ...
SSL Certificate definition: Digital credential authenticating website identity and enabling encrypted HTTPS connections. Learn how SSL/TLS certificates protect ...

Community discussion on HTTPS importance for AI search visibility. Webmasters share experiences with HTTP vs HTTPS sites and their impact on ChatGPT and Perplex...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.