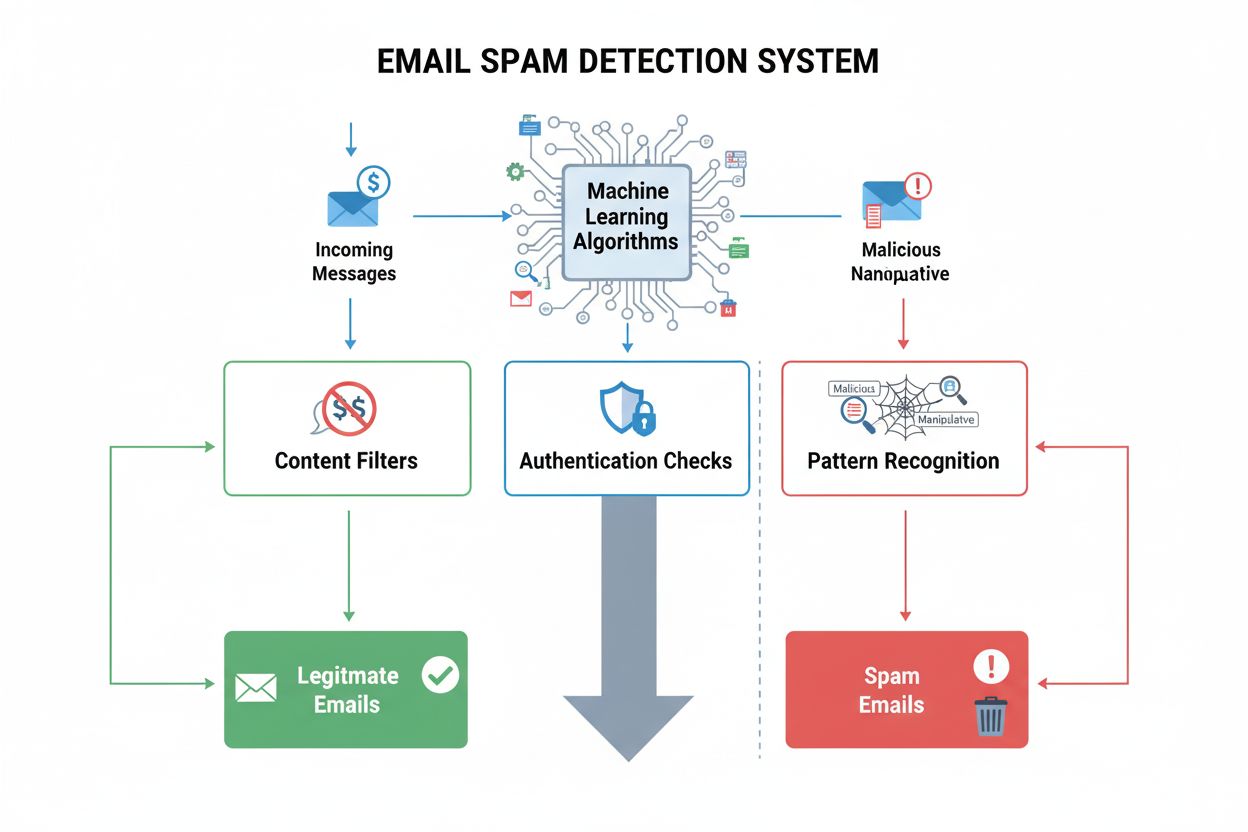
Spam Detection
Spam detection identifies unwanted, manipulative content using ML algorithms and behavioral analysis. Learn how AI systems filter spam across email, social medi...

Phishing is a fraudulent cyberattack that uses deceptive emails, text messages, phone calls, or websites to trick individuals into revealing sensitive information such as passwords, credit card numbers, or bank account details. It is a form of social engineering that exploits human psychology rather than technical vulnerabilities, making it one of the most prevalent and costly attack vectors in cybersecurity.
Phishing is a fraudulent cyberattack that uses deceptive emails, text messages, phone calls, or websites to trick individuals into revealing sensitive information such as passwords, credit card numbers, or bank account details. It is a form of social engineering that exploits human psychology rather than technical vulnerabilities, making it one of the most prevalent and costly attack vectors in cybersecurity.
Phishing is a fraudulent cyberattack that uses deceptive communications—primarily emails, text messages, phone calls, or fake websites—to manipulate individuals into divulging sensitive information or taking actions that compromise security. The term “phishing” derives from the analogy of fishing, where attackers use attractive “lures” (fraudulent messages) to hook victims. Unlike technical cyberattacks that exploit software vulnerabilities, phishing is a form of social engineering that targets human psychology, exploiting trust, fear, urgency, and curiosity to achieve malicious objectives. Attackers impersonate legitimate organizations, authority figures, or trusted colleagues to increase credibility and success rates. The stolen information typically includes usernames, passwords, credit card numbers, bank account details, or access credentials that enable further attacks such as identity theft, financial fraud, ransomware deployment, or network breaches.
Phishing attacks emerged in the mid-1990s as email became ubiquitous in business and personal communication. Early phishing attempts were crude and easily identifiable, featuring obvious spelling errors and generic messages. However, as cybercriminals refined their techniques and adopted more sophisticated tools, phishing evolved into a highly organized criminal enterprise. The sophistication of phishing attacks has accelerated dramatically in recent years, particularly with the advent of generative artificial intelligence (AI) and deepfake technology. According to IBM’s X-Force Threat Intelligence Index, attackers can now craft convincing phishing emails in approximately 5 minutes using AI tools, compared to 16 hours when done manually. This represents a 68% reduction in attack preparation time, enabling threat actors to scale operations exponentially. The evolution from bulk, indiscriminate phishing campaigns to highly targeted, personalized attacks demonstrates how cybercriminals continuously adapt to security measures and exploit emerging technologies.
The prevalence and impact of phishing attacks cannot be overstated. Research consistently demonstrates that over 91% of cyberattacks begin with a phishing email, making it the primary entry point for data breaches and network compromises. Additionally, approximately 75% of all cyber incidents originate from deceptive email messages, highlighting email’s role as the dominant attack vector. According to Huntress and industry research, over 90% of businesses globally experienced at least one phishing attack in 2024, and an estimated 3.4 billion phishing emails are sent daily worldwide. The financial consequences are severe: IBM’s Cost of a Data Breach Report 2024 indicates that phishing attacks cost organizations an average of USD 4.88 million per breach, making it one of the costliest attack vectors alongside compromised credentials. More than 80% of all reported security breaches involve phishing in some capacity, either as the initial compromise vector or as part of a multi-stage attack chain. These statistics underscore why phishing remains the preferred attack method for cybercriminals ranging from individual scammers to sophisticated organized crime groups and state-sponsored threat actors.
| Attack Type | Target Scope | Personalization Level | Delivery Method | Primary Objective | Success Rate |
|---|---|---|---|---|---|
| Bulk Email Phishing | Mass audience (thousands) | Generic/minimal | Credential theft, malware distribution | 2-5% | |
| Spear Phishing | Specific individuals | Highly personalized | Email, social media | Data theft, account compromise | 15-25% |
| Whaling (CEO Fraud) | C-level executives | Extremely personalized | Email, phone | Financial fraud, wire transfers | 20-30% |
| Business Email Compromise (BEC) | Organizations | Highly targeted | Monetary theft, data exfiltration | 10-20% | |
| Smishing | Mobile users | Moderate | SMS text messages | Credential harvesting, malware | 5-10% |
| Vishing | Phone users | Variable | Voice calls, VoIP | Social engineering, credential theft | 8-15% |
| Quishing | Public/physical spaces | Moderate | QR codes | Malware distribution, credential theft | 3-8% |
| AI-Enhanced Phishing | Targeted/mass | Highly sophisticated | Multiple channels | All objectives | 25-40% |
Phishing attacks operate through multiple technical and psychological mechanisms that work in concert to compromise security. Email-based phishing typically involves email spoofing, where attackers forge sender addresses to appear as legitimate organizations or trusted contacts. Attackers often use domain name spoofing, registering domains that closely resemble legitimate ones (e.g., “rnicrosoft.com” instead of “microsoft.com”) or using subdomains to create false legitimacy (e.g., “bankingapp.scamsite.com”). The phishing email itself contains carefully crafted content designed to evoke emotional responses—fear of account closure, greed from promised rewards, or curiosity about unexpected opportunities. Links within phishing emails direct victims to fake websites that replicate legitimate login pages with remarkable accuracy, capturing credentials when users enter them. Malicious attachments, often disguised as invoices, documents, or software updates, contain malware payloads such as ransomware, spyware, or backdoors that execute upon opening. Smishing (SMS phishing) exploits the trust users place in text messages, often impersonating banks, shipping companies, or government agencies. Vishing (voice phishing) leverages caller ID spoofing technology to make fraudulent calls appear to originate from legitimate organizations, with attackers using social engineering scripts to manipulate victims into revealing sensitive information or authorizing fraudulent transactions.
The business impact of phishing extends far beyond the immediate financial cost of a single breach. Organizations face operational disruption when systems are compromised, regulatory penalties for failing to protect customer data, reputational damage that erodes customer trust, and legal liability for inadequate security measures. The average time to identify and contain a phishing-related breach is 207 days, during which attackers can move laterally through networks, exfiltrate sensitive data, and establish persistent access for future exploitation. Small and medium-sized businesses (SMBs) are particularly vulnerable because they typically have fewer security resources and less sophisticated threat detection capabilities compared to enterprises. However, large organizations and government agencies are also frequent targets because the potential financial gain and intelligence value justify the attacker’s investment in sophisticated, targeted campaigns. Phishing attacks targeting the financial services, healthcare, and government sectors result in particularly severe consequences due to the sensitivity of compromised data and the critical nature of affected systems. The human element remains the most significant vulnerability: even with advanced technical controls, a single employee clicking a malicious link or opening an infected attachment can compromise an entire organization’s security posture.
The integration of generative AI and deepfake technology into phishing campaigns represents a fundamental shift in attack sophistication and effectiveness. AI-powered phishing uses language models to generate highly convincing, grammatically correct emails tailored to specific targets, eliminating the spelling and grammar errors that traditionally served as red flags. Voice cloning technology enables attackers to impersonate executives or authority figures in vishing attacks with remarkable accuracy, as demonstrated in a 2019 case where attackers used AI-generated voice to impersonate a CEO and defraud a bank manager of USD 243,000. Deepfake video technology creates fabricated video evidence of executives authorizing fraudulent transactions, adding another layer of credibility to social engineering attacks. Quishing (QR code phishing) exploits users’ trust in QR codes by embedding malicious links in codes posted in public spaces or sent via email, bypassing traditional email security filters. The Federal Trade Commission (FTC) has documented cases where criminals replaced legitimate QR codes on parking meters with fraudulent codes designed to steal payment information. These technological advances enable attackers to scale sophisticated, personalized attacks that previously required significant manual effort, fundamentally changing the threat landscape and requiring organizations to adopt more advanced detection and response capabilities.
In the context of AI-powered search and response systems like ChatGPT, Perplexity, Google AI Overviews, and Claude, phishing presents unique challenges for brand protection and information integrity. Attackers increasingly impersonate legitimate brands in phishing campaigns, leveraging brand recognition to increase credibility and success rates. AI monitoring platforms like AmICited track where brands appear in AI-generated responses, helping organizations detect when their brand names are being mentioned in contexts related to phishing, fraud, or malicious activity. This capability is critical because phishing campaigns often reference legitimate brands to deceive victims, and monitoring AI systems helps organizations identify fraudulent impersonation attempts before they cause widespread damage. Additionally, as AI systems become more sophisticated, there is a risk that phishing-related misinformation could be amplified through AI-generated content, making it essential for organizations to monitor how their brands are represented in AI responses. The integration of brand monitoring with AI citation tracking enables organizations to respond quickly to phishing threats, issue public warnings, and protect customer trust by demonstrating proactive threat detection and response capabilities.
The future of phishing threats will likely be characterized by increased sophistication driven by AI and automation, convergence of multiple attack vectors (email, SMS, voice, social media), and targeting of emerging technologies such as cloud services and mobile applications. As AI-powered phishing detection tools become more advanced, attackers will simultaneously develop AI-evasion techniques designed to bypass detection systems, creating an ongoing arms race between defenders and threat actors. Hybrid phishing attacks that combine multiple delivery methods and social engineering tactics will become increasingly common, requiring organizations to adopt more comprehensive, integrated defense strategies. The rise of supply chain phishing, where attackers target vendors and service providers to gain access to larger organizations, will necessitate stronger vendor security requirements and third-party risk management. Regulatory frameworks such as GDPR, HIPAA, and emerging cybersecurity mandates will increasingly hold organizations accountable for phishing-related breaches, driving investment in advanced detection and prevention technologies. Organizations that successfully defend against phishing will be those that combine advanced technical controls with continuous employee education, threat intelligence integration, and rapid incident response capabilities. The strategic importance of phishing defense will only increase as attackers continue to refine their techniques and exploit the human element as the weakest link in organizational security.
Phishing is a broad, indiscriminate attack sent to many recipients, while spear phishing is a highly targeted attack directed at specific individuals or organizations. Spear phishing attackers conduct extensive research on their targets using social media and professional networks to craft personalized messages that appear highly credible. Spear phishing has significantly higher success rates because of its tailored approach and psychological manipulation.
According to IBM's Cost of a Data Breach Report 2024, phishing attacks cost organizations an average of USD 4.88 million per breach globally. This figure includes direct costs such as incident response, legal fees, and regulatory fines, as well as indirect costs like reputational damage and lost business. The financial impact varies significantly based on industry, organization size, and the sensitivity of compromised data.
Common phishing types include bulk email phishing (mass emails impersonating legitimate brands), spear phishing (targeted attacks on specific individuals), business email compromise (BEC) attacks targeting organizations, smishing (SMS text message phishing), vishing (voice phishing via phone calls), and whaling (attacks targeting high-level executives). Each type uses different delivery methods and psychological tactics tailored to specific victim profiles.
Red flags include urgent language creating pressure to act quickly, requests for sensitive information or money, poor spelling and grammar, generic greetings instead of personalized names, suspicious sender email addresses or domains, unfamiliar links or shortened URLs, unexpected attachments, and mismatched branding. Legitimate organizations rarely request passwords via email or ask employees to verify credentials through unsolicited messages.
Generative AI tools enable attackers to create highly convincing phishing messages in minutes rather than hours, eliminating common red flags like spelling errors and grammatical inconsistencies. AI-powered voice cloning and deepfake technology add further credibility to phishing schemes. According to IBM's X-Force Threat Intelligence Index, AI reduces the time to craft a phishing email from 16 hours to just 5 minutes, significantly scaling attacker capabilities.
A multi-layered approach combining employee security awareness training, advanced email filtering, multi-factor authentication (MFA), and endpoint detection tools provides the strongest defense. Organizations should implement policies requiring verification of monetary requests through alternative channels, deploy DMARC and email authentication protocols, and conduct regular phishing simulations. However, employee education remains critical since no technical solution can prevent all social engineering attacks.
Phishing exploits human psychology rather than technical vulnerabilities, making it difficult to defend against with technology alone. Over 91% of cyberattacks begin with phishing emails, and approximately 75% of all cyber incidents start with deceptive email messages. Phishing provides attackers direct access to authorized users' credentials and systems, enabling them to bypass firewalls and security tools that would otherwise block external threats.
Phishing attacks frequently impersonate legitimate brands to increase credibility and success rates, making brand monitoring essential for detecting fraudulent use of company names and domains. Platforms like AmICited track where brands appear in AI-generated responses, helping organizations identify when their brand is being impersonated in phishing campaigns or malicious content. Monitoring AI systems for phishing-related brand mentions helps organizations respond quickly to threats and protect their reputation.
Start tracking how AI chatbots mention your brand across ChatGPT, Perplexity, and other platforms. Get actionable insights to improve your AI presence.

Spam detection identifies unwanted, manipulative content using ML algorithms and behavioral analysis. Learn how AI systems filter spam across email, social medi...
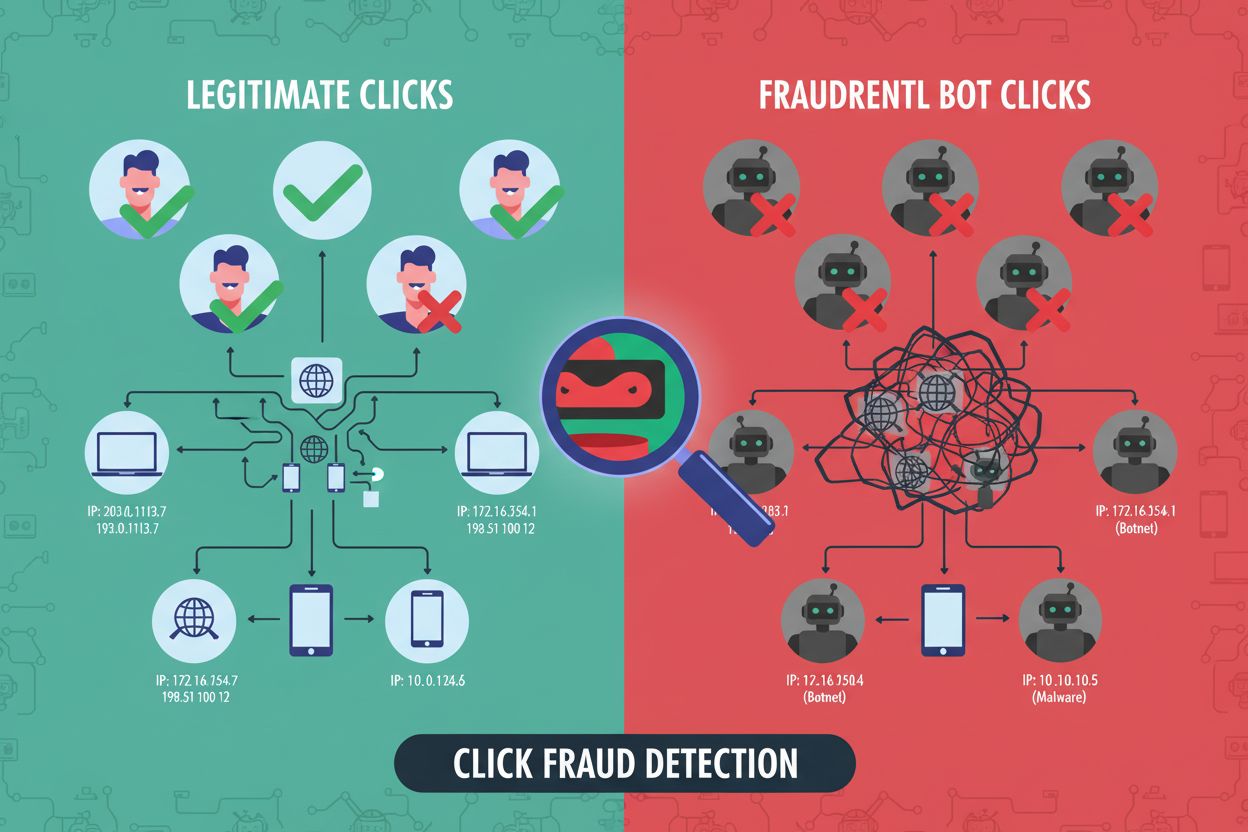
Click fraud is malicious fake clicks on PPC ads by bots, competitors, or click farms. Learn how it works, its impact on ROI, detection methods, and protection s...

Learn what keyword stuffing is, why it's harmful to SEO, how Google detects it, and best practices to avoid this black-hat tactic that damages rankings and user...
Cookie Consent
We use cookies to enhance your browsing experience and analyze our traffic. See our privacy policy.